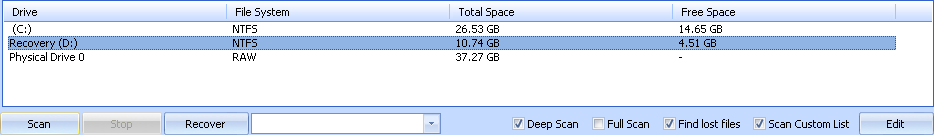
A bit more on the .xlr front
I was unable to find the .xlr file signature on the Web but I was able to use Recuva to get it, as follows:
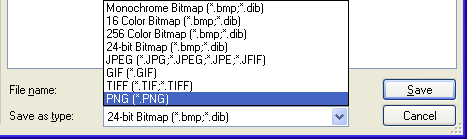
(1) I created a brand new hw.xlr file with Microsoft Works Spreadsheet (hw is short for hello world, in case you were wondering) and placed it on the desktop.
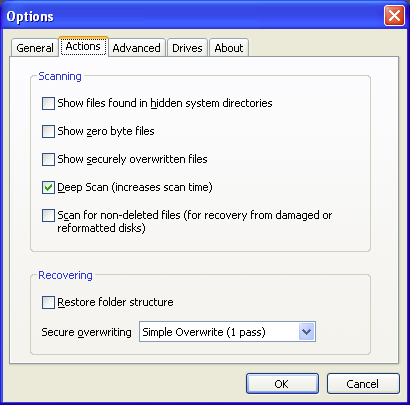
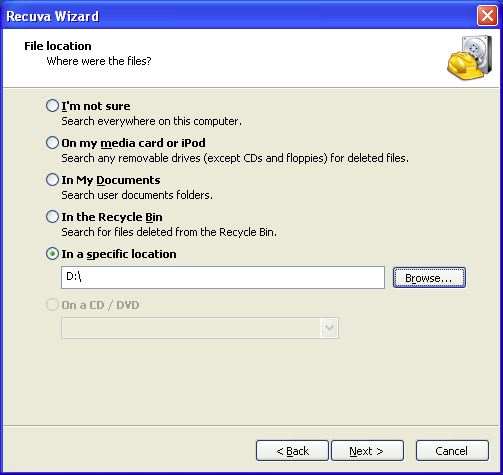
(2) I launched Recuva. In the advanced mode, I enabled the
Scan for non-deleted files (for recovery from damaged or reformatted disks)
option on the Options Actions tab.

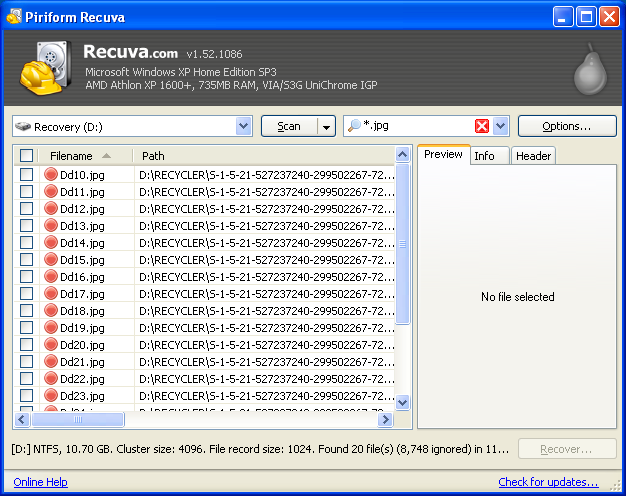
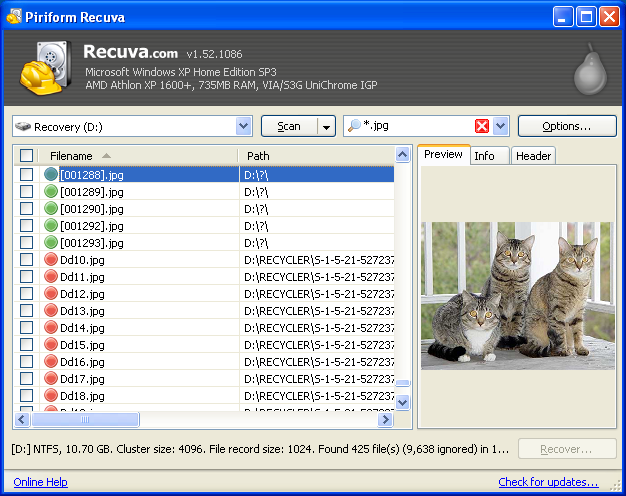
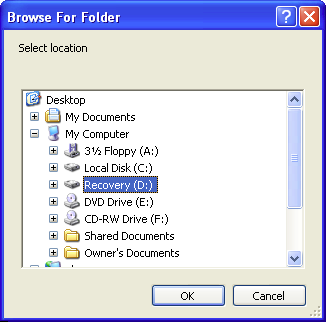
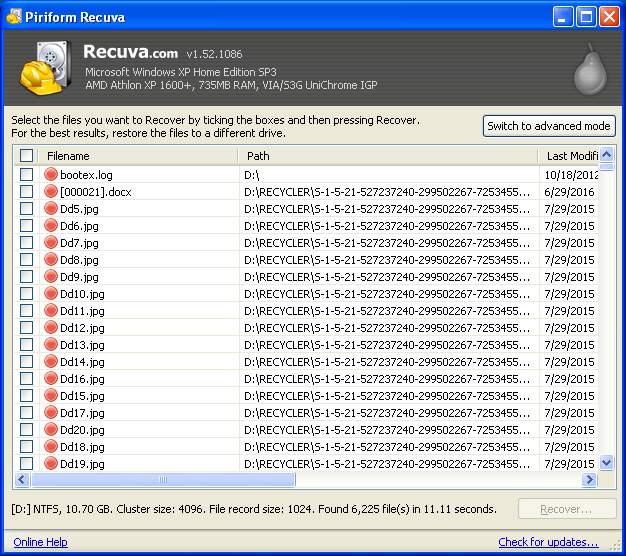
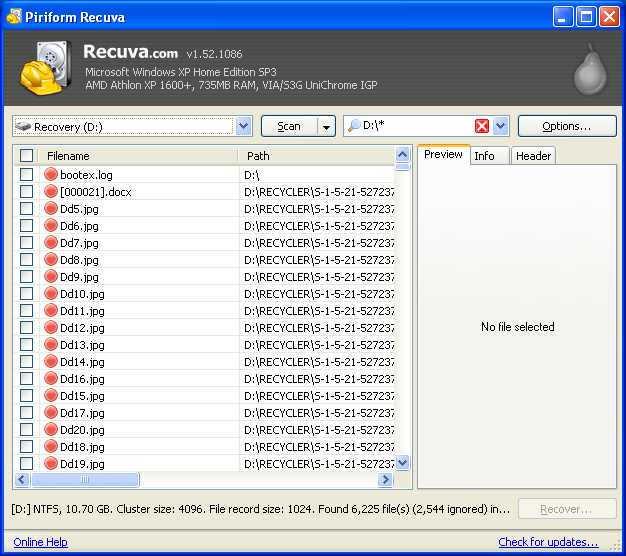
(3) In the main window I typed hw.xlr in the Filename or path search box and then ran a regular scan of the C:\ volume. The hw.xlr file duly came up; selecting it and clicking the Header tab on the right-hand side revealed its signature.

FWIW
(a) CTB-Locker left unmolested 6 My Documents\ .xlr files (cf. the Undamaged section of Part 3 of this series).
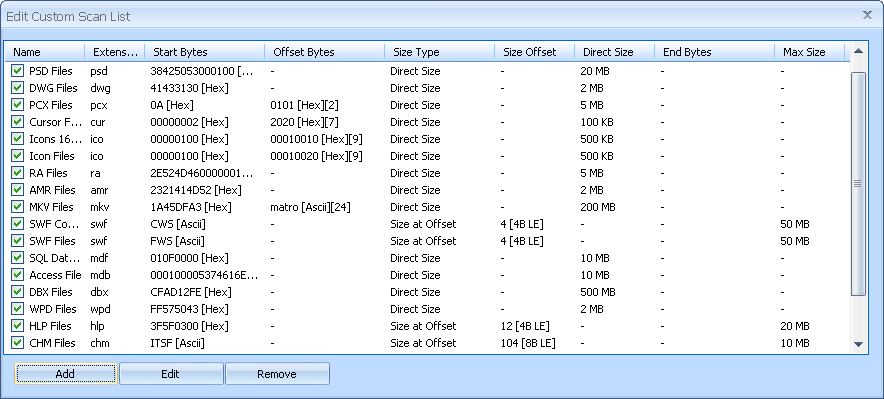
(b) As noted in the previous post, a .wps-enabled Puran File Recovery deep scan uncovered 6 ???\ .xlr files.
I go through the two groups of files: the (a) files are the same as the (b) files. Make of that what you will.
Taking stock of the .wps return
There are two My Documents\ folders in the D:\ volume:
(1) D:\02192015\My Documents\, which originally held 170 .wps files;
(2) D:\Compaq-09242012\My Documents\, which originally held 192 .wps files.
Upon comparing the Puran-recovered .wps files with the contents of these folders, it is clear that the recovered files came from the D:\Compaq-09242012\My Documents\ folder, giving us a (98 ÷ 192) × 100 = 51% recovery.
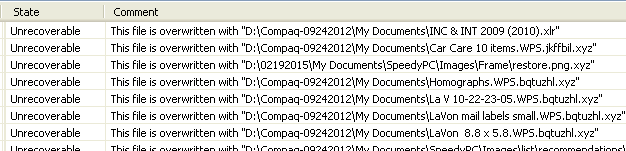
Interestingly, the recovered files and their numbers-names - 0003840.wps, 0003841.wps, ... 0003952.wps - closely track the last 98 A→Z Name-ordered .wps.*.xyz files in the D:\Compaq-09242012\My Documents\ folder: I can see a clear dividing line between what was recovered and what wasn't recovered. This being the case, my intuition tells me that the not-recovered files are gone for good, i.e., they've been permanently overwritten by either CTB-Locker or me, and that it would be a waste of time to try to find them with other file recovery tools.
As for the C:\ volume...
Some of you may be wondering, "Did you at least try to squeeze anything out of the C:\ volume?" It's a bit late for that, I'm afraid. In getting to this point, I've written to the C:\ volume and then deleted several batches of recovered .wps files, which does not bode well for finding those not-recovered files in the C:\ volume.
I nevertheless ran a .wps-enabled Puran File Recovery deep scan* of the C:\ volume a few days ago. This scan took 53 minutes and found 37,646 deleted files, of which 3,244 were ???\ .wps files, all in good condition. I wrote all of the .wps files to the D:\ volume and went through the first 10% of them: nothing new turned up at all. I'll try to look over the remaining files as time permits but I'm not gonna get my hopes up.
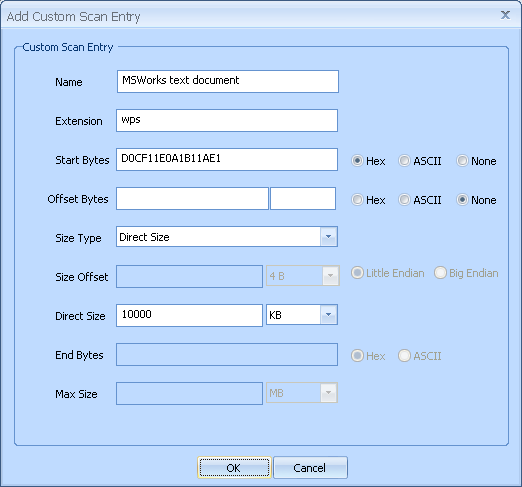
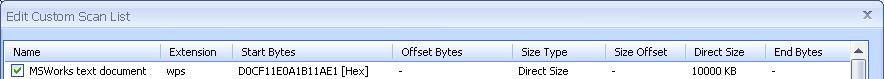
*For the purpose of recovery, the .wps profile's Direct Size setting was reduced to 255 KB; 3,244 10000 KB .wps files would not have fitted in the D:\ volume (or in the C:\ volume for that matter).
Repair redux
At the beginning of the year, just a few months before all of this happened, my father had repair work done on his computer by a nearby business called Modern Tech Computers. As to what necessitated that repair work, I don't know what specific problem the computer had but, this being a machine running Windows XP, I have no doubt it was malware-related.
I've got the invoice for the repair work in front in me, and the Description section thereof says that, in addition to "troubleshooting" and reinstalling a bunch of software, the repair person "backed up the user's data, pictures, documents, musics, favorites, and desktop". In practice:
(1) The Address Book\, Desktop\, Favorites\, and My Documents\ subfolders of the C:\Documents and Settings\Owner\ directory were copied to a new D:\02192015\ directory.
(2) Most of the C:\ volume was archived in a 02242015_full_b1_s1_v1.tib file, which was placed in a created-in-2012 D:\SystemBackup\ directory.
The 02242015_full_b1_s1_v1.tib file was created and can be opened by a program called Acronis True Image, whose free trial version I downloaded here.
The Documents and Settings\Owner\My Documents\ folder of the archived C:\ volume is stripped to the bone and doesn't contain any of the .wps/.jpg/.pdf files that the original C:\ volume did but at the same time there is a curious Documents and Settings\Owner\NetHood\ folder whose contents hint that the missing My Documents\ data may be stored 'in the cloud' (this is admittedly an area I am seriously behind the curve on) - does anything in the screenshot below look familiar to you?

The proprietor of Modern Tech Computers seems like a nice guy and he did what my father asked him to do; IMO he should have given my father a "You really should upgrade your system" take-home message, but he didn't.
If my father were interested in getting a new computer - and he isn't - I of course would recommend that he get a Macintosh. For about $250 he could buy a used Mac that has as much 'juice' (processor speed, hard disk capacity, amount of RAM) as his current computer and, crucially, would lift him out of the state of malware vulnerability he's presently in. I would ordinarily also tout a Mac's greater ease of use vis-à-vis that of a PC, but now that I am acclimated to my father's computer I'm not sure there's really that much of a difference between a Mac and a PC in this regard.
Not mentioned previously
Over and above its trojan payload, CTB-Locker placed a help_restore_files_btrne.txt file in a great many folders on my father's computer. The help_restore_files_btrne.txt files contain an
ALL your documents, photos, databases and other important files have been encrypted with strongest encryption RSA-2048 key, generated for this computer. ...message; a complete version of the message is posted at this Microsoft Community page.
I don't know what role, if any, these files play in the infection process - do they somehow flag sibling files for encryption, perhaps? In any case, let me note that Malwarebytes Anti-Malware did not get rid of them; they clearly shouldn't be present, and I manually deleted them one by one (there's probably a command-line way to delete them all at once but I'd have to do some homework on that).
Fin
When I began work on my father's computer in June, it was little more than a paperweight; thanks to Malwarebytes Anti-Malware, it's now running normally (well, as normally as could be hoped for given its age). Thanks to Recuva and Puran File Recovery, I was able to rescue about half of the .wps files, about ⅔ of the .jpg files, and almost all of the .pdf files that were encrypted by CTB-Locker on my father's computer; it would have been nice to recover everything although my inability to do so does have a silver lining in that it serves as a little object lesson in the importance of backing up data.
It is at long last time to move on. I want to get back to my 'technical' blog for a bit but I promise to return and write posts on
(a) the music I've been listening to recently and
(b) my employment situation
in the not-too-distant future.