On the Recuva Documentation's "Recuva FAQ (Frequently Asked Questions)" page, a • Fragmentation bullet point notes:
If a file is fragmented, you can recover it from an NTFS-formatted drive, but it may be less likely to be recovered.I accordingly begin by re-defragmenting the D:\ volume. FYI, I am now able to launch the Disk Defragmenter utility via the Start menu:
Start → Programs → Accessories → System Tools → Disk Defragmenter.
Regular
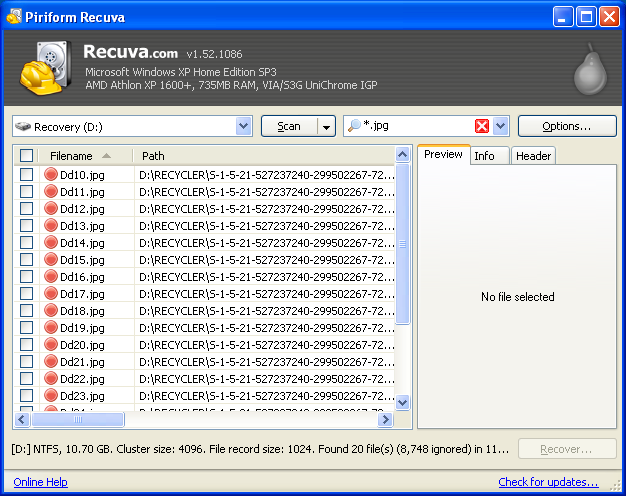
Subsequently, a regular scan of the D:\ volume finds 6,221 potentially recoverable files. In the advanced mode,
(a) a *.wps filter returns 0 files,
(b) a *.jpg filter returns 20 files, and
(c) a *.pdf filter returns 0 files.
All of the *.jpg hits are preceded by a ● circle indicating that their recovery is
unlikely.
See the Recuva Documentation's "Undelete and the Recycle Bin in Windows" page for a brief explanation of the Dd#.jpg name format.
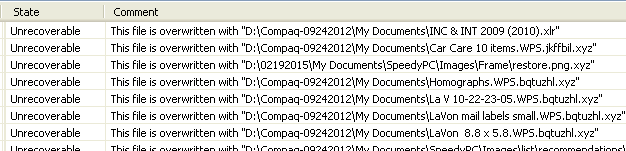
Horizontally scrolling the results field brings into view a State column that pronounces the Filename files "Unrecoverable" and a Comment column that provides a
This file is overwritten with "D:\pathname\filename.ext"
message for each file.
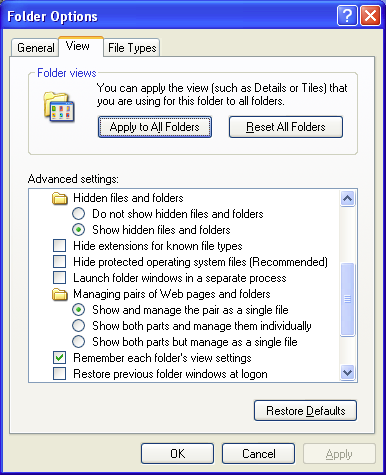
According to the Path column, the Filename files are located in the D:\RECYCLER\ directory, more specifically a D:\RECYCLER\5-1-5-21-527237240-299502267-725345543-1003\ directory. A RECYCLER\ directory is normally hidden but can be visibilized by checking the
Show hidden files and folders
radio button AND unchecking the
Hide protected operating system files (Recommended)
checkbox in the Advanced settings: menu on the View tab of the My Computer → Tools → Folder Options window.
A visit to the D:\RECYCLER\5...1003\ directory confirms that the Dd#.jpg files are well and truly gone - your guess is as good as mine as to why they turn up in the first place. I nonetheless try to recover a couple of them:
(1) I check the test files' checkboxes on the left-hand side of the results window; checking the checkboxes enables the currently disabled button in the window's southeast corner.
(2-3) I click the button: up pops a Browse For Folder window (see below for a screenshot), via which I place the files in the C:\ volume.
Double-clicking the recovered files' icons does launch the Windows Picture and Fax Viewer but all I see therein is a
No preview available
message vis-à-vis a rendered image.
Deep
The wizard-mode Thank you, Recuva is now ready to search for your files window tells us that we should run a "deep scan"
if previous scans have failed to find your files. For a deep scan, Recuva
look[s] through your drive bit by bit, more specifically, it
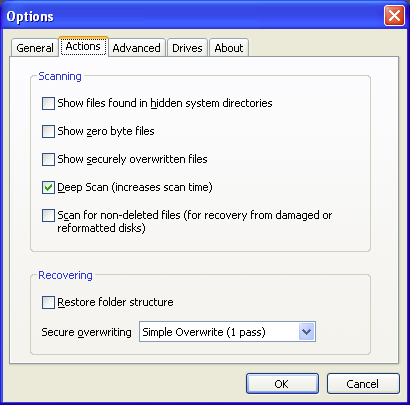
searches every cluster (block) of the drive to find file headers indicating the start of a file. Let's get a deep scan under way, then, shall we? We can enable a deep scan (toggle from a regular scan to a deep scan) by either
(a) checking the
Enable Deep Scan
checkbox in the wizard-mode Thank you... window or
(b) checking the
Deep Scan (increases scan time)
checkbox on the Actions tab of the advanced-mode Options window.
A deep scan of the D:\ volume (which takes ≈ 20 minutes vis-à-vis ≈ 12 seconds for a regular scan) finds 7,516 potentially recoverable files. In the advanced mode,
(a) a *.wps filter returns 0 files,
(b) a *.jpg filter returns 425 files, and
(c) a *.pdf filter returns 21 files.
The Recuva Documentation's "Deep Scan option" page specifies those file (extension) types that can be identified by a deep scan and .wps isn't one of them, so it's not such a surprise that our search didn't return any .wps files.
Regarding the *.jpg hits, the Dd#.jpg files are still there but now we also have 405 files that are linked to a ?\ directory and whose prospect of recovery is excellent: they're preceded by a ● circle, the State column pronounces them "Excellent", and their Comment column messages read No overwritten clusters detected. For almost all of the ● files, clicking a file name displays an image preview on the Preview tab on the right-hand side of the results window.
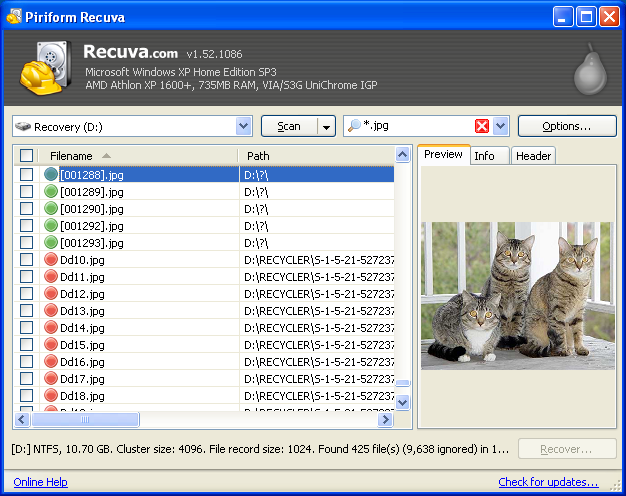
The ● files have a [#].jpg name format because, per the aforecited "Deep Scan option" page,
a deep scan can only recover files, not [original] file names.
It gets better: I am able to pick out 64 ● files that contain photos belonging to my father's pre-CTB-Locker collection of My Documents\ .jpg photos. (The Options → View mode → Thumbnails View is helpful in this regard.) I check the files' checkboxes and click the button. In the Browse For Folder window I go to the C:\ volume and then click the button, which creates a New Folder\ directory, which I rename Recuva rescued images\.
I click the button and then go to
My Computer → Local Disk (C:) → Recuva rescued images
to see how it all came out: quite gratifyingly, the recovered files are good to go.
So, 64 out of 100 - not quite Meat Loaf's standard but I'll take it. Mitigating circumstances regarding the missing files:
• I don't know what state those files were in to begin with.
• Their .jpg extension notwithstanding, I don't know if they really were .jpg images versus some other image format (e.g., .bmp, .gif) or, for that matter, if they really were 'pure' images versus documents that commingled images and text.
• Some of the original photos were duplicates.
• Finally, I can't rule out that I didn't pick out all of the relevant Recuva results.
As for the *.pdf hits, their prospect of recovery is excellent as well; they don't give previews so I recover the entire lot as described above (I put them in a Recuva rescued documents\ directory). They're OK too, and all of them belong to my father's pre-CTB-Locker set of My Documents\ .pdf files.
I am able to recover some of the original .wps files via a different file recovery program and I'll tell you all about it in the following entry.
Remind me to email you when my computer crashes because I admit my eyes were kind of glazing over as I read through the heroics you have expended in a effort to rescue your father's files. Just don't roll your eyes at me like my 20-something blogger son does when I ask him what he considers a dumb tech question. "Excuse me, let's remember who taught you to use a spoon, young man." I did go back to post #1 in this series to find out what disaster had sparked the need for this mega-intervention. Yikes! I'm just starting to hear about ransomware---mostly from a scary commercial on TV. So, here's my question: I run Norton on my lap top, a Lenovo Think Pad. Is that enough to catch ransomware?
ReplyDelete